 This is the continuity of my first blog post How I Indexed the Darknet and Pastebin During My First University Internship. The GoSecure Torscraper was developed about 1 year ago. Due to a few issues, the entirety of the project was dockerized to simplify the installation procedure (~4-8 lines instead of 4 pages of documentation) and to automate the whole scraping process. With this upgrade, it makes the tool easier to use by everyone. Once the project was dockerized, I started analyzing the collected data and it goes without saying that it was the most interesting part of this project.
This is the continuity of my first blog post How I Indexed the Darknet and Pastebin During My First University Internship. The GoSecure Torscraper was developed about 1 year ago. Due to a few issues, the entirety of the project was dockerized to simplify the installation procedure (~4-8 lines instead of 4 pages of documentation) and to automate the whole scraping process. With this upgrade, it makes the tool easier to use by everyone. Once the project was dockerized, I started analyzing the collected data and it goes without saying that it was the most interesting part of this project.
Before starting my analysis, I tried to put myself in the place of a person that has never gone on the Darknet or that has minimal knowledge about it, and I questioned myself about it. Every time I did, it was always that same question: What is the Darknet made of?
Most people probably have the same general idea about it: It is full of illegal things like drugs, weapons, fake documents, and hitmen. Is it possible to find more than that? With this analysis, it is possible to have a glimpse of what the Darknet is made of. This blog post is all about my journey in analyzing Darknet data: what I found, how surprised I was and what I believe is going on. Then a rationale on why we will stop maintaining FreshOnion TorScraper will be presented before concluding with my thoughts on the Darknet.
Drugs, Guns, fake documents, etc. – As expected
If you need to hire someone to kill your neighbor, to buy an AK-47, to get fake documents to exit the country or to get your next dose of cocaine, there is one place to get all these — on the Darknet. Are these topics as present as people think? Of course, as when surfing on our index, I encountered several markets and websites selling these things or these services.
Looking into our TorScraper’s feed:
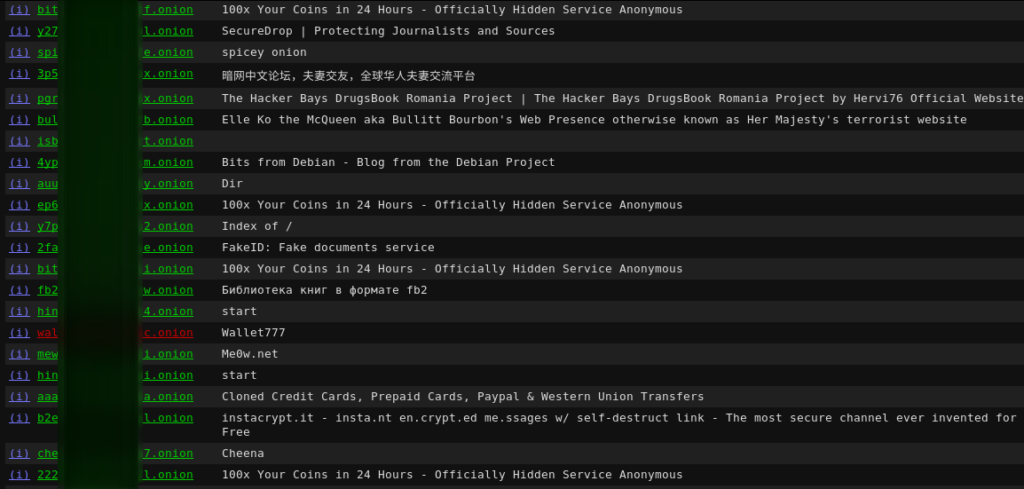
This screenshot illustrates the concept precisely.
-
- 4 Bitcoin’s multiplicators
- 1 Hacker/Drugs website
- 2 Fake documents services
In this case, 7 links are linked to drugs, weapons, Bitcoin, fake documents on a total of 22 links (~32%). I believe that this screenshot is a good way to illustrate the expected topics of the Darknet.
Talking about expected things, it could be interesting to talk about Bitcoin. It is the principal cryptocurrency used on the Darknet, but is it only used to pay bills? I do not think so.
Since Bitcoin became more popular, a new concept was created. Its name is, “Bitcoin’s multiplicator”. It is simple, you give your bitcoin to someone you do not know and “he will give you back” 100 times the value you sent him within 24 hours.

“All you have to do is to transfer some Bitcoins to address listed below (we do not accept investments below 0.005 Bitcoins) and your investment will be multiplied hundredfold and will be transferred to your wallet within 24 hours.”
Would you give $1 dollar to an unknown person in the street and hoping to have a 100$ dollar bill back? Probably not, which is why it seems to be a scam.
Mystery Box – I unbox it for my YouTube channel
Is the concept of Mystery box familiar to you? Have you already heard about it? If not, the concept is pretty simple. You are buying a box that is full of unknown things. Now let’s add the Darknet aspect to make the concept of the mystery box more exciting, intense and horrible at the same time. Do people sell that on the Darknet? Yes, Here is an example of a website selling Mystery Boxes.
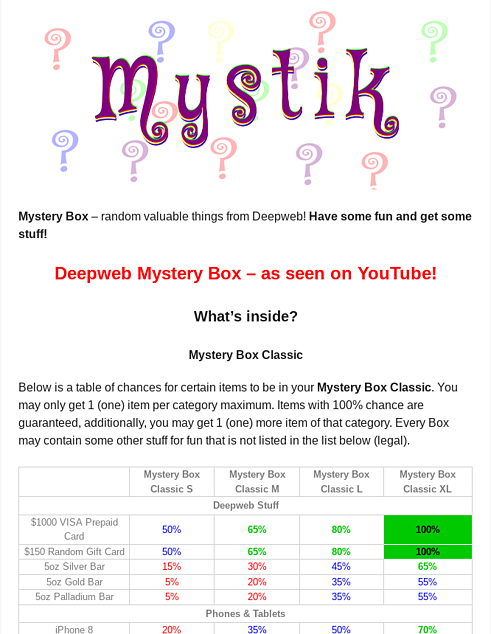
Mystik (in the example above) is showing the content and the possibility of obtaining specific items, but all not “mystery box” websites allow such flexibility. As you can see there are different types of boxes (size, content, etc.), the price also depends on the one selected. The main reason I think this concept works is that it enables people to produce engaging video content. In regards to video content, YouTube and social media come to mind.
Nowadays, social media occupies a large space in our lives and people are capitalizing on the idea that the Darknet is an illegal, dangerous, mysterious arena to promote themselves on different platforms (YouTube, Facebook, etc.). Most people showing Darknet content on YouTube exaggerate the gravity of what they have seen to get more hits. And what is currently trending on YouTube? You probably guessed it, MYSTERY BOXES! People are buying Darknet Mystery Boxes and unboxing them on YouTube. Generally, people are getting horrible things trying to scare viewers. Like in this YouTube video , a guy received a screwdriver with some kind of red liquid on it.

It is probably red paint, but it could be blood. The fact is if you received a screwdriver in a mystery box from the Darknet you probably think, or want to persuade people that it is blood to get more views.
Below is another example of a website selling these boxes on the Darknet.
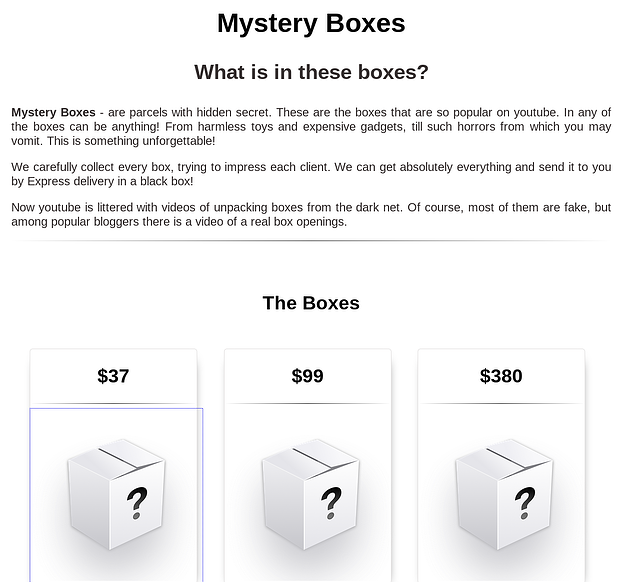
“In any of the boxes can be anything! From harmless toys and expensive gadgets, till such horrors from which you may vomit. This is something unforgettable!”
After my research, I did not find many websites selling mystery boxes, but there are numerous YouTube videos showing YouTubers unboxing them. I suppose there could be more websites selling them; however, it is possible that people are creating their own to get views as well.
Forums – Want to talk about it?
Once I have finished watching people unboxing real or fake mystery boxes, I should start looking for something more concrete, forums.
Please note that people normally link Tor to the Darknet, but Tor is not only used for illicit purposes. Users can use Tor to navigate anonymously on the web, meaning on sites that are not hosted on the Darknet. Such user anonymity is sometimes crucial when one resides in a country with high internet censorship. On the other hand, onion hosting services allow one to host a website anonymously, but the content doesn’t necessarily have to be illicit.
During my research, I found an interesting forum named Galaxy3. This forum is about cybersecurity, technology, and geek subjects. Also, the administrator created Galaxy, a competition for the forum’s community. In this competition, users need to create a hidden website or a Web application. At the end of the competition, the community judge all the projects and the three best ones receive a price. I found this concept great and I believe that it brings members of the forum closer because it is also possible for projects to be made in teams of four.
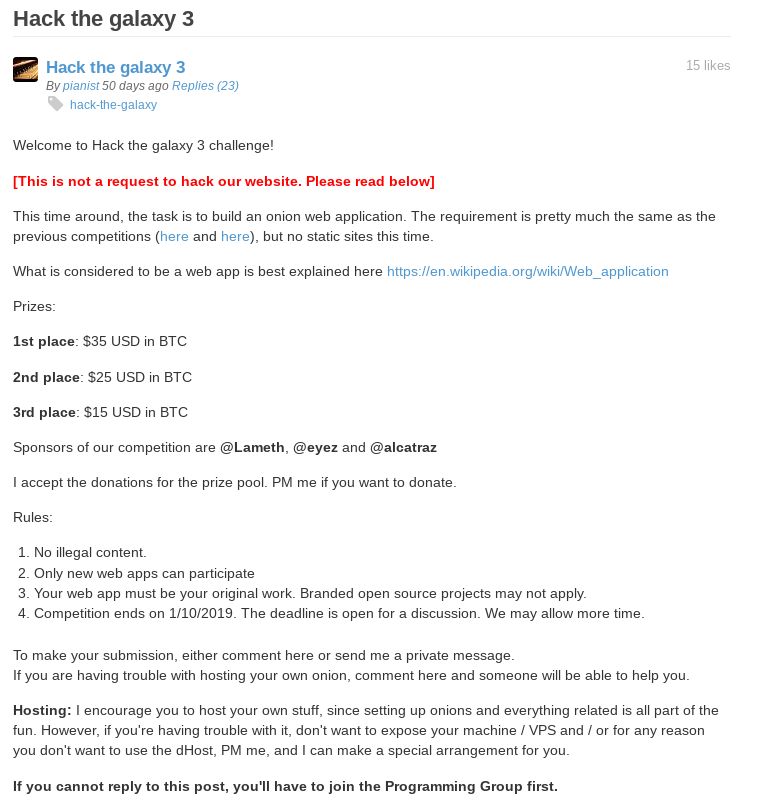
Despite the fact that people associate Darknet to illegal things, it does not mean that no rules are imposed. Normally, administrators impose some restrictions and rules on their forum to keep control of it. This is an example of “The terms of services” alias rules of the Galaxy3 forum:
http://galaxy3m2mn5iqtn.onion/terms
The terms of service are pretty much following the rules. 🙂
1. No images of children. Including 3D or cartoon. Use your common sense, if in doubt ask before you post. DO NOT ask for these things either, you will be banned.
2. No public commercial trade. We don’t want Galaxy3 turning into a market place targeted by Government agencies. Even harmless commercial trade will not be allowed, because what might be legal in your country may not be legal in another. This includes advertising, job offers, scams, or buying goods and services.
3. No pornographic content and / or gore in public areas (This includes sites linking to illegal content). Legal (18+) pornography / erotica and gore are allowed in closed groups.
4. Images and avatars are considered public content, so rule 1. and rule 3. apply.
5. No doxing or posting anything that may endanger someone.
6. Do not solicit members into committing a crime. This includes, but not limited to, hacking and carding requests.
7. Do not advertise criminal internet resources (clearnet or hidden) – by linking to them on the wire, in a blog post, in a group or other. This includes, but not limited to, the sites that contain illegal pornography, fraud, illegal vendor shops and markets.
8. Be respectful. Galaxy is a respectful community, allowing Freedom of Speech. Harassment will get you banned. Too much disrespect will get you banned. Use your common sense.
9. Do not spam. This is self explanatory.
10. Do not scam. This includes cyber begging. If you’re running a legit charity, please consult the staff before advertising it.
11. Do not advertise extremist / terrorist material. If it’s considered extremist / terrorist anywhere on the globe, it will be deleted and result in insta-ban for the user posted.
12. No public sex ads. This is not a dating site. The posts on the wire / groups / blogs will be removed. Repeated offenses will result in deletion of your account.
13. My word is law. If I decide something, that is what it will be. I will have the final say in everything. I am also open to discussing the rules. I too make mistakes, I am human as well. I will not ban you if I disagree with you, you can approach me with concerns, and we can talk about it. I am a very open minded person. If you feel treated unfairly, come to me. I want Galaxy3 to be for everyone.
Normally when someone transgresses them, he will be banned for a specific period of time. Once again, the duration of punishment is at the discretion of the administrator.
Otherwise, it is not always this type of forums that users find. Here are other examples of forums that I found during my journey.
Markets – Shut up and take my money!
Markets on the Darknet are a place where sellers and buyers encounter to trade all kinds of things or services such as drugs, fake documents, weapons, hacking services, etc. Also, they usually use Bitcoin or any other kind of cryptocurrencies as payment to be as anonymous as possible. There are also many things that make markets trustable or not. Do I need to log in? If yes. Does it have an option to enable 2-factor authentication? Does it use the concept of escrow? These concepts could influence a user’s decision of using one market instead of another, so let’s take a look at them.
Log in
The majority of websites that sells services or items will require users to authenticate themselves. It is easier to track their orders or to rate/review sellers and customers. In the opposite case, markets that don’t require authentication generally ask to communicate by email to proceed the order. In my opinion, this ordering system is much harder to trust because there are no reviews and forums to help customers judging vendors’ products.
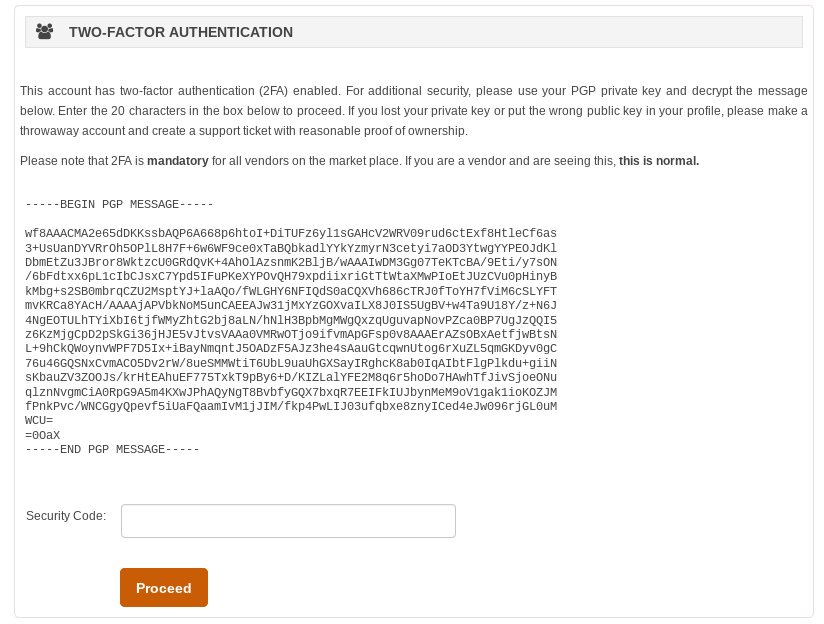
The 2-Factor Authentication Dilemma on the Darknet
It is not always possible to have this security option, but on some sites, the user can enable it. Normally 2-factor authentication will require an email, a phone number, or an application but theses techniques directly lead to the user’s identity. To counter this problem, the user needs to add his/her public key to his/her profile to enable 2-factor authentication. The public key will be used to encrypt a message that contains a security code. Once the user gets authenticated, he/she will receive the encrypted message. The only way to decrypt it is by using his/her private key.
Escrow
This is a service used on different market to secure funds until both sides (customer and vendor) complete the transaction. The customer will send funds to the escrow. The escrow will hold funds until the customer confirms that he/she received the package or the service. At this time, the escrow will send the money to the vendor. In case of dispute, the customer will need to defend his/her points with evidence. Using a third-party escrow is not free, normally the intermediary takes a percentage of the transaction. According to this source, it varies between 1% and 5%.
The markets that implemented these concepts have an advantage over the others because users are looking for security and anonymity when they are buying or selling items or services. They certainly do not want to be traced. Find below examples of markets that I found during my journey.
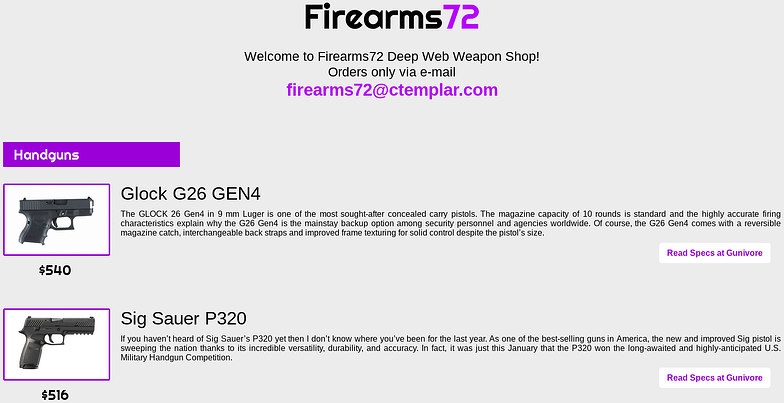 Firearms72
Firearms72
The first one is a website that sells weapons. The way to order a weapon is via e-mail because there is no authentication process.
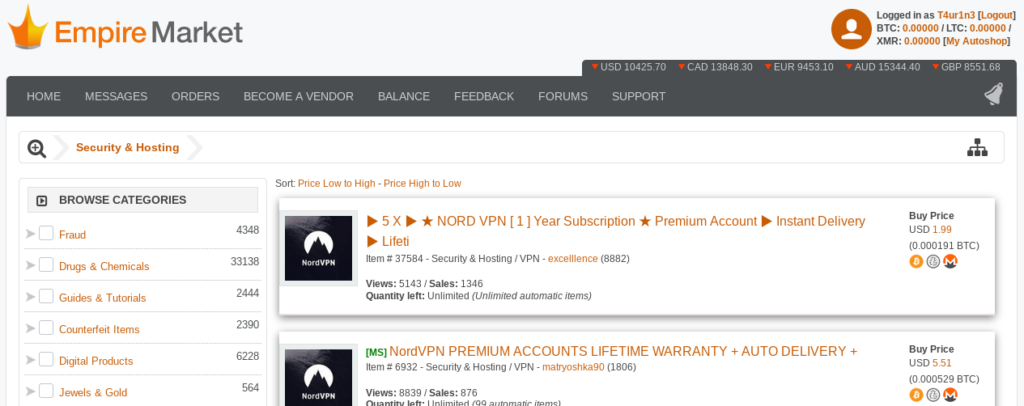 Empire Market
Empire Market
The second one is a big market that sells pretty much everything that is illegal. Users are able to authenticate themselves and they have the option to enable 2FA. It also has a message option to communicate with vendors or customers, users’ orders are tracked and there is a forum linked to this market.
Overall, if one day I need to buy something illegal, I will probably look at a market like Empire instead of Firearms72 because it seems more serious, professional and secure.
Dark side – When I lost faith in humanity …
This section is about all the horrible things that I found on the Darknet during my analysis. From child pornography to red rooms.
Just a reminder: The Torscraper is a crawler that visits domains and stores ONLY the content in raw HTML, so no pictures or videos are stored. Now that this is explained, let’s start with child pornography. When a domain is visited by the crawler, it looks at the title of the site and the content of its pages. If the title contains one or multiple words that are in our banned words list, it will set the domain as banned. It means that the content on this domain may be child pornography and we do not want this domain to be indexed.
Child Pornography
During my analysis, I counted 177 domains that are banned. Potentially, this number should be bigger because there are many more that have not qualified as banned but contain child pornography. Simply by reading at a site’s title, it is not always obvious whether it contains child pornography or not. Sites could hide contents behind a normal title to keep a low profile.
Now an example that illustrates this concept, one day, I was looking at our Kibana dashboard to see what information was collected. Among the list of collected domains within the last 5 minutes, I noticed a title named “Sumo Gay Sex”. What an unusual title for a site! I was curious, so I decided to look at the extracted text, and I found this:
WELCOME to SUMO GAY SEX
CLICK HERE TO ENTER
BY ENTERING YOU AGREE TO THESE TERMS:
If you are likely to be OFFENDED by any of the representations described below or if you are UNDER 18 years of age, DO NOT PROCEED. You must be at least 18 years of age to enter this site. Upon entering our site YOU AGREE that: You have been warned about the nature of the material, thus waiving any action against the operators of this site, for encountering anything you may find offensive and that you must be Eighteen years of age or more. This website contains HARDCORE STUFF with YOUNG BOYS AND OLDER MEN all are real life characters, all stories or situations are true. No play no fake.
THE AGE OF OUR MODELS IS 14 to 60.
All content on this site was banned in clear web so be warned THIS IS HEAVY STUFF. All is >forbidden and tasteless.
All content Copyright 2014 to 2017 by Sumo Gays DW, All Rights Reserved.
CLICK HERE IF YOU DO NOT AGREE TO THE TERMS
Based solely on the title of the page, I would have never expected that this site contains child pornography. Sites’ appearances can be deceiving.
Slave Trafficking
Of course, you can buy many different things like drugs, weapons, fake documents and much more on the Darknet, but what about humans? Slave trafficking is present on the Darknet. There are several sites that are operating that kind of business. I found ~30 domains containing slave trafficking and 26 of them are the same website and probably hosted by the same person. Looking at the raw HTML, I noticed that girls between 14 and 18 years of age are sold. It is not explicitly said that these girls are sex slaves but read the text stripped from one indexed slave trafficking website and judge for yourself:
Slave Girls for Cash – Hire a slave girl
The girl is brought to the place you choose
To have a slave girl contact slavegirls@XXXXXXXXXX.XXXXXX
Hire for 15 days: 1490€/1590$
Hire for 30 days: 2790€/2980$
The slave girl will fulfill ALL your wishes 24/7 for the specified period of time
Sharon, age: 16, from Hungary, Currently Available
Bonnie, age: 15, from Romania, Currently Available
Jolanda, age: 17, from Poland, Currently Available
Chloe, age: 15, from USA, Currently AvailableJenny, age: 16, from USA, Currently Available
Karina, age: 16, from Poland, Currently Available
Jess, age: 15, from USA, Currently Available
Miki, age: 15, from Russia, Currently Hired, NOT Available
Michelle, age: 16, from France, Currently Available
Annie, age: 17, from Poland, Currently Available
Judith, age: 17, from France, Currently Available
Irina, age: 17, from Russia, Currently Available
Katy, age: 17, from USA, Currently Available
Pamela, age: 15, from Ukraine, Currently Available
Virginia, age: 14, from USA, Currently Available
Kim, age: 18, from USA, Currently Available
Nicole, age: 15, from Argentina, Currently Hired, NOT Available
Sarah, age: 18, from Russia, Currently Hired, NOT Available
The girl is brought to the place you choose
If you have particular requests about age, body, ethnicity, etc. ask us
To hire or BUY a slave girl contact slavegirls@XXXXXXXXXX.XXXXXX
Red Room
And Red Rooms, what about that? Are they real or not? For those who have not heard about that before, a red room is supposed to be a room where someone gets tortured live on camera while spectators place bets on the victim. The one with the highest bid will decide what will be done to the tortured person. It sounds horrible, right? We indexed 31 Red Room sites, and 30 of them are mirrors. Overall, I am very skeptical about their existence, and there are several reasons why.
Joining a red room is simple, first users need to select from types of access, Spectator (standard), Commander and Master. Once the type of access has been selected, users will be redirected to a page such as this one:
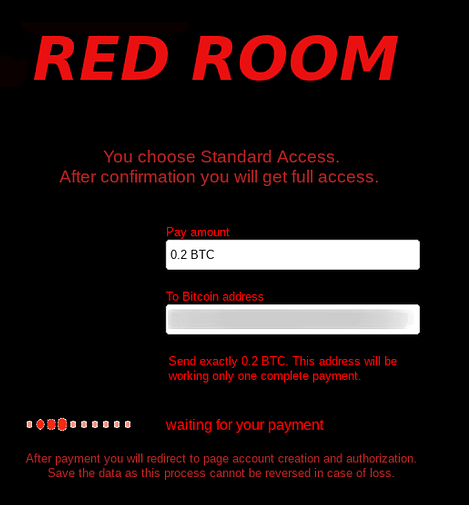
“Send exactly 0.2 BTC. This address will be working only one complete payment.”
But how will they know that I sent them 0.2 BTC? There is nothing to identify me to the transfer. I also came back on this site several days later and they modified their interface. They added transaction IDs to look more legitimate, but since they are reusing bitcoin addresses among IDs, anyone can easily see that this is a scam.
Secondly, Tor allows users to surf anonymously so a site with no login won’t be able to trace a bitcoin transaction back to its visitor. Also because internet traffic using the Tor protocol will go through many volunteer servers -known as nodes- (for more information see the Tor website), it makes the connection slower, so it could be painful to chat and see the live stream without any delay.
Thirdly, are people paying for that? I investigated the bitcoin addresses to see if someone ever paid for that service. So I made a script to get all bitcoins addresses from the red room sites that we indexed. The script created a list of 18 bitcoins addresses. Then I looked into the blockchain for each address to see the amounts of bitcoin they received. Without any surprises, all these addresses had received less than the requested amount of 0.2 BTC (~ 2378,38 USD). The average amount they received was 0.002 BTC (~ 237.84 USD) which is far below the requested value. Also, a minority of the addresses collected (6) were not in the blockchain, it means that no bitcoin had been transferred to these addresses.
For all these reasons, I believe that red rooms are fake.
Retiring our Fork of FreshOnion TorScraper
At GoSecure, we have been maintaining the open source Tor indexer called FreshOnions TorScraper for little over a year now. Doing so we have gained an understanding of what we can gain by monitoring the Darknet. As a cybersecurity vendor in the endpoint and email space with professional services, it turns out that indexing the Darknet isn’t useful in protecting our clients.
Our friends at the Montreal startup called Flare Systems created a product called FireWork. It supersedes what we had deployed internally greatly. We are now using what their platform for Darknet assesments and research.
Overall, maintaining a Darknet crawler is time-consuming and effort-intensive. Because of that and due to the small overall gain for our clients we will archive our version of the FreshOnion TorScraper project. If you would be interested in taking over the maintenance of the project contact us. We will happily refer to your project here and on our GitHub.
Darknet – As I see it now
Overall, the Darknet is not as scary as people say because markets, hitmen, mystery boxes, and others are, in my opinion, mainly surface concepts to scam people. As I said before, the Darknet is mainly a jungle full of scammers in which the best will make money out of it, and the others will lose theirs. Still, some websites are deeply concerning and deserve police attention. For complete transparency, a list of URLs was reported to the police.
Finally, I believe that an additional portion of the Darknet could be scary, but this one is probably not easily accessible to most of us, because we do not know the .onion domain names. Darknet sites are accessible because someone announced that domain on the clear Web, in a private IM conversation or on a known Darknet website. Otherwise it would be very unlikely for us to guess these domains as they are generated randomly and are 16 characters long. For the sake of simplicity lets assume 16 characters representing 32 values (.onion uses base32 encoding) and that there is one million .onion services, this gives one chance in roughly one billion billion of guessing a valid domain. Now, with the new generation of .onion services using 56 characters, guessing a valid Darknet domain is one chance out of 1 quinvigintillion (1×1078). Good luck with that!



