Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders: Importance versus Implementation
In the survey, respondents were asked about multifactor authentication (MFA), a security measure requiring that a user presents at least two factors, such as: “something that you know” and “something that you have”, before being granted access to a system. When asked, on a scale from 1 to 5, how important multifactor authentication is for the security of their organization, 93.3% said important or very important. When asked whether such a measure was implemented in their organization on their external network, 45% replied yes, 41.7% partially, and 13.3% no, as shown in Figure 1.
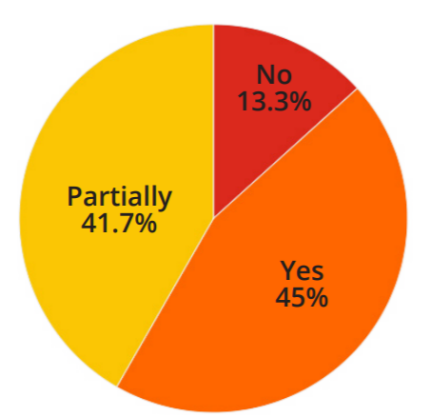
Figure 1 -Multi-Factor Authentication at the External Perimeter
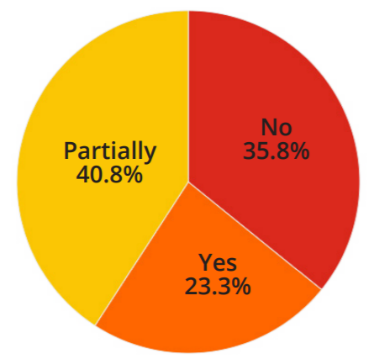
Figure 2 – Multi-Factor Authentication at the Internal Perimeter

Figure 2 – Multi-Factor Authentication at the Internal Perimeter
Pentesters’ Experience
We then asked our pentesters their perspective and experience with multifactor authentication. According to them, penetration test results show that multi-factor authentication is very efficient at blocking attackers. However, such a measure must be implemented on all externally exposed services, not only the email service, the most common MFA location. Moreover, they mentioned that it is important to note that a secret question is not a second factor: a password and a secret question are both based on a user’s knowledge. Each factor must come from a different authentication vector: a password is what one knows, and an RSA OTP (One Time Password) number is what one has, for example.
Moreover, GoSecure pentesters were surprised that 23% of the respondents said that they implemented multi-factor authentication on the internal network, as they have rarely encountered such security measures in organizations internally. They added that even if critical services have two-factor authentication, day-to-day activities are usually unprotected, such as RDP access to servers or file share access.
Pro Tips on Multifactor Authentication
As a reference for readers, below are some pro tips related to implementing multifactor authentication on corporate networks.
- Focus on implementing multifactor authentication on all services.
- SMS-based multi-factor authentication is better than single-factor authentication.
Keep in mind that for critical services that could be targeted by highly motivated attackers, SMS-based multi-factor authentication could be bypassed using a technique called SIM Swapping. - An affordable multi-factor authentication solution is the use of software tokens. These rely on an application on your phone or a computer containing a secret feed instead of relying on a physical token like an RSA key. This is one of the cases where open source solutions exist, but their management and integration are relatively complex. You might consider using a commercial solution if ease of implementation is a concern.
Be aware that the information sent to the user to enroll the token can sometimes be reused by an attacker if the attacker gets access to it. Thus, it is important to encourage users to destroy the file or email once they have registered their software token.
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.


