This blog post summarizes the results of a study that sheds light on ordinary workers conducting benign IT tasks, such as developing websites or translating texts, that contribute to cybercrime activities. The researchers from multiple organizations, including the GoSecure Titan Labs team, conducted a thematic analysis and used machine learning, as well as statistical tests on several datasets, to extract a general understanding of these workers and their mass effect.
This blog post summarizes the results of a study that sheds light on ordinary workers conducting benign IT tasks, such as developing websites or translating texts, that contribute to cybercrime activities. The researchers from multiple organizations, including the GoSecure Titan Labs team, conducted a thematic analysis and used machine learning, as well as statistical tests on several datasets, to extract a general understanding of these workers and their mass effect.
Rarely do researchers have access to private conversations between individuals involved in cybercrime. Consequently, we are left imagining or speculating how those behind cybercrime live, what motivates them or how they overcome the daily challenges related to their criminal activities. Sporadic media accounts report successful stories of cybercriminals making millions and living in mansions. However, this sweet life may not be the representative of the majority of individuals involved in cybercrime (the mass).
In the past two years, a member of the GoSecure Titan Labs research team who has since moved on to an academic position, Masarah Paquet-Clouston, led a study on cybercrime motivations and contexts. The study sheds light on ordinary IT workers having connections with cybercrime. Understanding the role of these workers is often forgotten in the cybersecurity industry, as most researchers are interested in new juicy nation state threat actors. Yet, these workers are key actors in the cybercrime ecosystem: they form a large population of individuals who continuously contribute to cybercrime, without necessarily having an “attacker mindset”.
This study uncovered such workers, and their ties to cybercrime. It was conducted in collaboration with Serge-Olivier Paquette, from SecureWorks, Sebastian Garcia from Stratosphere Laboratory and Maria Jose Erquiaga from Cisco Systems. The results were first presented at Blackhat USA 2021. Following the presentation, the team summarized (and refined) the research results and submitted a manuscript to the Oxford academic journal: Journal of Cybersecurity. The article, titled Entanglement: Cybercrime Connections of a Public Forum Population, was accepted and published in July 2022
Private Chats: An Insider’s View on Cybercrime Participation
 The research started with access to private discussions, discovered by the Stratosphere Laboratory, among individuals (mainly three) involved in spreading the Geost botnet, an Android banking trojan malware. The conversations illustrated a rather tedious and monotonous reality for what seemed like hardcore cybercriminals at first sight. Precisely, these individuals were developing websites to distribute banking trojan applications.
The research started with access to private discussions, discovered by the Stratosphere Laboratory, among individuals (mainly three) involved in spreading the Geost botnet, an Android banking trojan malware. The conversations illustrated a rather tedious and monotonous reality for what seemed like hardcore cybercriminals at first sight. Precisely, these individuals were developing websites to distribute banking trojan applications.
To understand their motivations and challenges, the team conducted a thematic analysis of the conversations and the main themes found were that these individuals were:
- Facing an adverse business environment
- Conducting amateur work
- Had a leniency towards criminality
These sample quotes reflect the themes:
- “Well, nothing you can do. You should always be prepared. This business is not stable”
- “Our sites are not high-quality, they will not last long”
- “Conversion rate is different, but there is no guarantee that total sum will be better than from legal”
In the end, the individuals we studied in private conversations were ready to do anything for a small payment. They were not the masterminds behind the Geost botnet, but rather those at the bottom of the cybercrime supply chain, helping with malware distribution. The criminal minds behind the Geost botnet need an army of such workers to effectively spread their malicious applications.
These individuals likely represent the reality of cybercrime participation for many!
More details about the private chat log analysis can be found in the Blackhat USA 2021 presentation.
Public Chats: An Insider’s View on How Cybercrime Participation
The private conversations analyzed pointed towards searchengines.guru (hereafter named the public forum) “[…] a website allowing users to discuss issues related to creating and promoting websites on the Internet”. The website, at first sight, looked legitimate. Rarely do researchers have access to these two sides: private and public conversations. The team dived into the public forum to understand how these three individuals used it, and also to understand the forum’s population potential connections with cybercrime. More details about the following analyses can be found in the article referenced above.
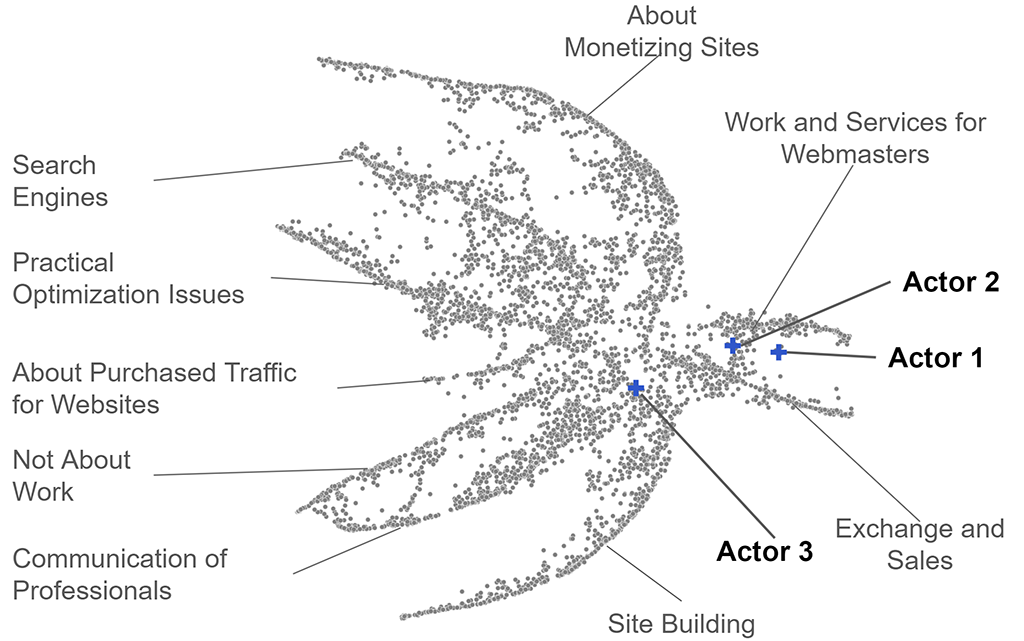
To do so, the team used academic access to Flare Systems’ database, a company that develops a digital risk protection and cyber threat intelligence platform. The dataset created included all individuals who commented on the forum in 2017 and 2018. First, to visualize the forum and assess where the actors were positioned in it, a map of the forum population was created using UMAP: Uniform Manifold Approximation and Projection for Dimension Reduction, as shown in Figure 1.
The representation carries valuable information. The (x,y) coordinates are not directly interpretable but the relationships between points are important. Figure 1 shows a set of arm-shaped groups that stretches from the center to the outside. The shapes of the groups are informative, as the groups that take the shape of long and narrow arms represent users that comment mostly in one category, with the most active users at the outer ends of the arms. The team investigated each of the arms in the map to find the dominating public forum category on that arm. These groups define mostly in tight communities, some with very active users, commenting several thousand times over the span of two years, as in the Site Building category.
Actors 1 and 2 are close to the categories: Work and Services for Webmasters and Exchange and Sales. These two have much shorter arms that are closer together, indicating that less users in these categories were very active contributors to their communities, hinting at a more opportunistic behavior. Actor 3 is positioned in the center: there is nothing special about him, just part of the mass. The team conducted a content analysis of the three actors’ conversations and found that all three were typical actors who used the forum to covertly develop their illicit business aimed at spreading banking trojan applications. However, they did NOT talk about their malicious activities publicly on the public forum. They used a LEGAL forum (where informal sales take place) to develop their cybercrime activities. This sparked the question:
How many others are like these individuals? Is this common?
Proxy for Cybercrime Participation: Drifters
 To answer this new inquiry, the team developed a key concept: drifters (note that the term drifter changed to crossover user in the article). Drifters are individuals from the public forum who also had conversations in cybercrime forums.
To answer this new inquiry, the team developed a key concept: drifters (note that the term drifter changed to crossover user in the article). Drifters are individuals from the public forum who also had conversations in cybercrime forums.
How many drifters are there on the public forum? To identify them, the team created various timeframe and username filters and searched for forum users in the Flare Systems database who also commented on cybercrime forums and found that: 7.2% of forum users were drifters!
Also, the cybercrime forums on which drifters participated were quite diversified, including Nulled.to (cracking and leaks), DarkMoney (money laundering), BestHackForum (hacking), ExploitIn (hacking), Blackhat World (black hat SEO), club2crd (carding) and more. So, how active were drifters in cybercrime forums?
Limited Involvement
 Based on the data gathered, the involvement of drifters in cybercrime forums was quite limited. Drifters posted, on average, 21 comments on cybercrime forums (std=75), with a minimum of one and a maximum of 1,383. More importantly, 50% of drifters posted three comments and 75% posted only ten comments. They only dipped a toe in cybercrime forums!
Based on the data gathered, the involvement of drifters in cybercrime forums was quite limited. Drifters posted, on average, 21 comments on cybercrime forums (std=75), with a minimum of one and a maximum of 1,383. More importantly, 50% of drifters posted three comments and 75% posted only ten comments. They only dipped a toe in cybercrime forums!
Clearly, drifters’ involvement in cybercrime forums was limited.
Hidden in the Mass
Once drifters were identified, one last line of inquiry remained: “Are drifters special in the public forum? Do they represent a specific subgroup?”. First, Figure 2 shows the forum map with drifters indicating that they are all over the place. To confirm this conclusion, the team developed posting behavior indicators, including activity rate, diversification level and topics of interests, and then conducted a series of statistical tests to see if drifters and non-drifters differed based on these indicators.
The results of these analyses were quite straightforward: drifters are indistinguishable –at least based on the indicators developed. This forced the team to conclude that either drifters are part of the mass of users, behaving the same way, like the three individuals in the private conversations, or the number of drifters is higher, and the filters developed were too conservative.
Conclusion
The results of this study have two main key takeaways. First, there is a need to look beyond cybercrime forums to understand cybercrime participation. Many tasks surrounding cybercrime, such as developing websites to spread malicious applications, are legal. It’s how the criminal uses them that is illegal. And for many, there is NO NEED to go on cybercrime forums to find answers to questions related to cybercrime tasks at hand, just like the three actors studied in this analysis.
Second, given that drifters’ involvement in cybercrime forums is limited and that they are part of a mass of workers looking for business opportunities, like the three actors studied in the private conversations, an interesting policy recommendation would be to change their opportunity landscape. These workers are looking for business opportunities, and as a group, they enable cybercrime operations to have reach (more victims) and increase the sophistication (more infections through various infection vectors). Focusing on preventing this mass from drifting into cybercrime could prevent a lot of damage beforehand. Obviously, this is not a simple task, and that is why cybersecurity researchers are constantly working to uncover new social patterns behind cybercrime. Stay tuned!
If you have any questions about the research methods, you can either refer to the Blackhat USA 2021 presentation or the scientific article titled Entanglement: Cybercrime Connections of a Public Forum Population and recently published in the Journal of Cybersecurity. The article details the second part of the research on the drifter population, dubbed crossover users in the paper.
About the Author: Masarah Paquet-Clouston was part of GoSecure Titan Labs for five years prior to completing her PhD and securing an academic job at Université de Montréal in criminology. During her time at GoSecure, she completed several large-scale studies on cybercrime and cybersecurity, including understanding the misaligned incentives between defenders and attackers in cybersecurity (presented at SecTor 2020), and uncovering the industry of social media fraud driven by malware (presented at BlackHat USA 2019 and RSA 2019). She is still a close collaborator of GoSecure Titan Labs.